SPECIFICATIONS:
1. Encryption / Decryption Server
1) Sever Linux OS
2) Adopted essential method of ARIA in Domestic National Dept.
3) Apply Symmetric key (secret key) method
4) Adopted (ARIA-GCM-128), which applied Confidentiality, Integrity, Authenticity, Audit Functions
5) Adopted function of Non-Repudiation
6) Communication Method : TCP/IP
7) Adopt Key Access Module
2. TCP/IP Communication DLL Software
1) Communication Method : TCP/IP
2) Provide simple solution of the Encryption decryption sever communication
3) Provide User’s API
DESCRIPTION:
1. Fundamental security requirements applied
◆ Confidentiality
- Ensures only intended recipient(s) can understand a message or decode
- private data; protect meter keys & usage data
◆ Integrity
- Messages and data are preserved without change; prevent attacks on the metering network by enabling meters to detect false
commands
◆ Authenticity
- The origin of messages and commands can be proven; messages are not replayed
◆ Non-repudiation
- The sender of a message cannot deny sending it
◆ Authorization/Administration
- Policy control; sender of a request/command is authorized to do so
◆ Availability
- Device and network resources cannot be overloaded or flooded with bogus commands; e.g. system redundancy
◆ Audit
- E.g. Secure logging to enable detection of tampering or unauthorized access
2. Special environment of Smart Water Grid
◆ As the communication environment is relatively poor than SG(Smart Grid),
secret key (symmetric key) method might be used.
◆ Considering battery power method using algorithms that maximizing the electric power
◆H/W module’s security key at each place should be downloaded at specified security place in advance with considering installation
situation of each place.
3. Security Module – Applied the following Algorithms
◆ Hash Function(Integrity, Authentication) = SHA256
◆ MAC(Integrity, Authentication) = HMAC-SHA256
◆ Block Cipher (Confidentiality) – Base Encryption = ARIA
◆ Block Cipher (Confidentiality) – Block Cipher = GCM (Galois Counter Mode)
◆ Random Number Generation(Authentication) = CTR-DRBG
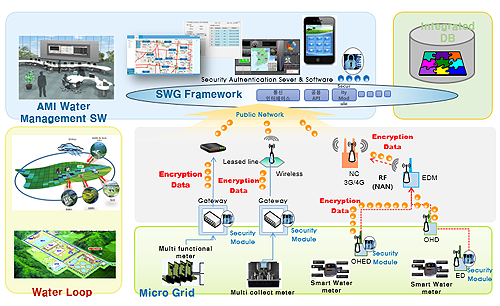














Share Security Authentication server&software in Social Media